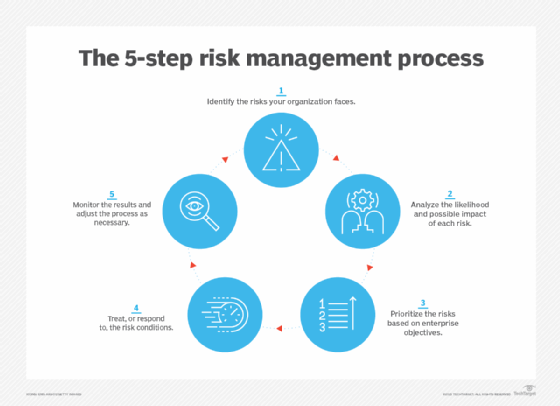
5 core steps in the risk management process
Implementing an effective risk management process is a key part of managing business risks. Follow these five steps to ensure a successful process.
Risk represents any kind of uncertainty that can affect an organization's ability to achieve its business objectives. There are many forms of business risk, including ones that involve projects, finances, cybersecurity, data privacy, regulatory compliance and environmental factors. Such risks aren't all negative -- there are also positive ones that present business opportunities. For both, you need a planned, purposeful approach to understand and then manage the balance between risk and reward.
Risk factors can have a big impact on how businesses operate -- and whether they can continue to do so in an effective way. The ability to navigate risk better than competitors will certainly contribute to a company's success. Failure to do so could spell disaster, perhaps beyond recovery. For these reasons, applying a proven and consistent process for managing risk, built on a solid enterprise risk management (ERM) foundation, is a must.
Perhaps the best-known risk management process is the one outlined by the International Organization for Standardization, or ISO as a common acronym across different languages. ISO 31000, its risk management standard, includes extensive information on how to communicate about, manage and report on various risks. The process is essentially the same for any type of entity and includes the following five core steps for documenting, assessing and managing risks.
1. Identify risks
The first step in the risk management process is to determine the potential business risks your organization faces. That requires some context: To consider what could go wrong, one needs to begin with what must go right. Start the risk identification phase with a review of business goals and objectives and the various resources or assets that enable them. Risk management practitioners often apply a top-down, bottom-up approach to thinking about what might impede those objectives.
The top-down portion considers mission-critical business activities that shouldn't be impaired, such as sales transactions in a retail store or manufacturing processes in a factory. It then lists the conditions that might impair those programs. For the bottom-up portion, the members of a risk management team can consider various known risk sources, like natural disasters, ransomware attacks or an economic downturn, and the impact they might have on the organization.
A potential risk is only a real risk if it would have a business impact. For example, NISTIR 8286A -- part of a series of reports on integrating cybersecurity risks into ERM programs published by the National Institute of Standards and Technology (NIST) -- listed the following four elements that must be present to describe a negative cyber-risk:
- A valuable asset or resource that could be affected.
- A source of a threatening action that could act against the asset.
- A preexisting condition or vulnerability that enables the threat source to act.
- Some harmful impact that occurs from the threat source exploiting the vulnerability.
With building blocks of that sort, risk managers can create a broad set of risk scenarios to be analyzed, prioritized and treated later in the process. An example risk scenario might be, "The manufacturing plant is affected by a power outage resulting from a tropical storm, disrupting plant operations for several days." Such scenarios provide useful insight into what risk events might occur in the future.
As part of identifying risks, it can also be helpful to review news headlines and other available information about risks that similar businesses have faced. In addition, various types of risk can be organized into categories. That enables each type to be considered and tracked by individuals or teams familiar with the particular issues that are involved. For example, categories could include strategic risk, financial risk, compliance risk, operational risk, people risk and technology risk, among others.
For each risk category, a defined process for developing risk scenarios will ensure that the resulting list of identified risks is sufficiently comprehensive. Many tools are available to help visualize the scenarios. Examples include the following:
- A risk breakdown structure, which is a type of chart for listing project risks in a hierarchical way.
- Value stream mapping and affinity diagrams for visualizing critical business assets and relationships -- for example, as part of Carnegie Mellon's OCTAVE Forte risk management methodology.
- Delphi technique exercises for considering investment and other risks through a series of questionnaires sent to a group of participants.
The final component of the risk identification step is to record the findings in a risk register. It provides a means of communicating and tracking the various risks throughout subsequent steps. The NIST report series cited above includes an example of a risk register, along with a sample risk detail template in which many of the results of the risk management process can be recorded for an individual risk.
2. Analyze the risks
The second step of the risk management process is to analyze how likely it is that a risk will occur and whether it will have a measurable impact on the organization. There's a whole science to risk analysis, but essentially it involves calculating the probability of a risk event or scenario and estimating the potential consequences if that happened.
While there is often an immediate impact, there could be other subsequent consequences, as well. Each of these factors must be considered in the analysis. For example, take the loss of a laptop containing patient health records. There's the immediate equipment loss, but a breach of that patient data could result in fines, lawsuits and reputational damage that far exceed the cost of the device.
Risk analysis should also include time factors as a part of the calculation. Financial reporting systems are often considered critical, but during tax preparation time their integrity and availability needs might be particularly important. The frequency of risk events is another time-based factor to consider.
Many organizations express the level of risk found during an analysis in general, or qualitative, ways. Terms such as high risk or low probability are often used, or red-yellow-green color schemes. Organizations might also benefit, though, from a more quantitative approach to risk analysis. For example, the Factor Analysis of Information Risk (FAIR) model, documented in the Open Group's Open FAIR standard, can be used to perform detailed cyber-risk calculations that could be more helpful in assessing risks than color-coding.
There are dozens of methods available for both qualitative and quantitative risk analysis. Many of them are described in IEC 31010, a standard on risk assessment techniques that is jointly developed and published by ISO and the International Electrotechnical Commission (IEC) as a complement to ISO 31000.
3. Prioritize risks based on business objectives
The results of the risk analysis stage enable the various risks to be sorted and ranked based on their importance to the organization. Since risk management resources are likely to be limited, risk evaluation and prioritization highlights the risks that are most likely and would be most impactful. Plotting the results in a risk heat map -- also known as a risk assessment matrix -- helps to visualize the relative importance of each risk. That can benefit both the risk management team and business stakeholders, including those who may be providing or authorizing resources to respond to the risks.
While the initial prioritization of risks might be based on the combination of likelihood and impact, the final ranking could be influenced by factors that are important to the stakeholders who are involved. For example, if senior management has expressed that customer trust is a key value for the enterprise, risks that might affect customers could be prioritized above others.
4. Treat the risks
With a prioritized list of risks in place, the next step is to evaluate the options available to treat, or respond to, the risks and decide which approach to apply in each case. Potential risk treatment actions including the following:
- Risk acceptance. If a risk is deemed to be acceptable based on business leadership's risk appetite, no further treatment is necessary.
- Risk sharing or transfer. This involves sharing some of the potential impact of a risk with another entity, such as an insurance firm or an external service provider -- or, if possible, completely transferring responsibility for the risk to that entity.
- Risk mitigation and control. Where practical, various risk mitigation measures and management, technical and administrative controls can be applied to help reduce the likelihood or impact of each risk to an acceptable level.
- Risk avoidance. If none of the other options are feasible, risk managers must implement risk avoidance measures to eliminate the activities or exposures that would enable a particular risk scenario.
Be sure, though, that the risk treatment methods being applied are both effective and cost-effective. The resources required to treat the risk should be commensurate with the assets being protected. That's why a bank might use a 20-cent chain to protect an ink pen and a million-dollar vault to protect its cash reserves.
5. Monitor and review risk management results
After the above steps are completed, the results of initiatives must be tracked and monitored to ensure that risks are managed effectively and remain within acceptable limits. In addition, risk conditions can change rapidly, the value of strategic assets can fluctuate and the risk preferences of business executives can evolve. A critical part of risk monitoring and review is ensuring that business managers and senior leaders are informed about progress toward risk management goals and any relevant changes that might have organizational impact.
With this as the final step, the process of managing risk is similar to the PDSA Cycle. Short for Plan-Do-Study-Act, it was popularized during the second half of the 20th century by W. Edwards Deming, an academic and quality improvement consultant. In this context, regular monitoring and review enables continual improvement of the risk management process. As various teams throughout the organization work to identify, analyze, prioritize and respond to risks, the results inform possible refinements for the next iteration of their efforts.
Creating a successful risk management process
While these steps are relatively straightforward, every business has unique requirements and attributes that affect how it should manage risk. To incorporate them into risk decision-making, it's helpful to implement a risk management framework as part of a comprehensive approach to managing the various risks an organization faces.
Also, keep in mind that the goal of the risk management process, in the context of a broad framework, is not to completely eliminate all risk but to determine acceptable levels of it and then work to keep individual risk factors within agreed-upon boundaries. Doing so should be based on business objectives and a balance between business opportunities and the limits spelled out by executives in risk appetite and risk tolerance statements.
With that as a foundation, organizations can use the five steps detailed here to consistently identify and prioritize the risks that are likely to have a harmful business impact; apply risk mitigation and control strategies or adopt other treatment methods; and monitor the results for continual improvement and success.
Greg Witte is a senior security engineer at Huntington Ingalls Industries Inc. His work includes helping organizations integrate cybersecurity risk considerations into enterprise risk management programs.








